En esta guía, se explica cómo configurar Wireshark y ejecutar Pyspinel para olfatear paquetes de una red Thread.
Para usar el complemento extcap de Wireshark para el espionaje de paquetes, consulta Espionaje de paquetes con extcap.
Configura el entorno del sniffer
Antes de comenzar, completa los siguientes pasos:
- Revisa los requisitos de espionaje de paquetes.
- Instala y configura Wireshark.
- Instala Pyspinel y las dependencias sin extcap.
Compila el sniffer
Compila y escribe en la memoria flash un dispositivo NCP para que funcione como sniffer con el resultado binario ot-rcp.
Nordic nRF52840
Para configurar el ejemplo de Nordic nRF52840 para usarlo como sniffer, clona
openthread/ot-nrf528xx y configura el entorno de compilación:
git clone https://github.com/openthread/ot-nrf528xx --recursive./script/bootstrap
Establece la tasa de baudios en 460800. Busca la línea #define UART_BAUDRATE NRF_UARTE_BAUDRATE_115200 en src/nrf52840/transport-config.h y reemplázala por #define UART_BAUDRATE NRF_UARTE_BAUDRATE_460800.
Compila el objeto binario:
./script/build nrf52840 UART_trans
Convierte el resultado binario ot-rcp en hexadecimal:
arm-none-eabi-objcopy -O ihex build/bin/ot-rcp ot-rcp.hex
Programa el archivo ot-rcp.hex en la placa nRF52840 como se detalla en Cómo programar el nRF52840.
Inhabilita el dispositivo de almacenamiento masivo (MSD) en el nRF52840 para evitar problemas con la corrupción o la pérdida de datos cuando uses el puerto de depuración:
expect <<EOFspawn JLinkExeexpect "J-Link>"send "msddisable\n"expect "Probe configured successfully."exitEOF
spawn JLinkExe SEGGER J-Link Commander V6.42b (Compiled Feb 5 2019 17:35:31) DLL version V6.42b, compiled Feb 5 2019 17:35:20 Connecting to J-Link via USB...O.K. Firmware: J-Link OB-SAM3U128-V2-NordicSemi compiled Jan 7 2019 14:07:15 Hardware version: V1.00 S/N: 683411111 VTref=3.300V Type "connect" to establish a target connection, '?' for help J-Link>msddisable Probe configured successfully.
Propiedades de la red de Thread
Antes de continuar, obtén las siguientes propiedades de la red Thread que deseas sniffear. Las necesitarás para configurar Wireshark y ejecutar el sniffer de Pyspinel.
Prefijo local de malla
Para obtener el prefijo local de malla de un dispositivo en la red Thread de destino, haz lo siguiente:
Usa la CLI de OpenThread:
dataset activeMesh Local Prefix: fd33:3333:3344:0/64Usa
wpanctlcon un NCP:wpanctl getprop IPv6:MeshLocalPrefixIPv6:MeshLocalPrefix = "fd33:3333:3344:0::/64"En la GUI web de OTBR, selecciona Estado. El prefijo local de malla aparece como IPv6:MeshLocalPrefix, similar a
wpanctl.
Canal
Para obtener el canal de un dispositivo en la red Thread objetivo, haz lo siguiente:
Usa la CLI de OpenThread:
channel15Usa
wpanctlcon un NCP:wpanctl getprop NCP:ChannelNCP:Channel = 15En la GUI web de OTBR, selecciona Estado. El canal aparece como NCP:Channel, similar a
wpanctl.
Clave de red
Wireshark usa la clave de red de Thread para desencriptar los paquetes después de la captura. Para obtener la clave de red de un dispositivo en la red Thread de destino, haz lo siguiente:
Usa la CLI de OpenThread:
networkkey33334444333344443333444433334444Usa
wpanctlcon un NCP:wpanctl getprop Network:KeyNetwork:Key = [33334444333344443333444433334444]
La clave de red de Thread no está disponible en la GUI web de OTBR.
Opciones de sniffer
| Opciones | |||||
|---|---|---|---|---|---|
-u or --uart |
|
||||
-c or --channel |
|
||||
--no-reset |
|
||||
--crc |
|
||||
-b or --baudrate |
|
||||
--rssi |
|
||||
--tap |
|
||||
Ejecuta el sniffer
Asegúrate de usar la ruta de acceso del dispositivo específica para tu NCP y el canal de la red Thread que intentas rastrear.
Si sigues esta guía, el DK nRF52840 se debe conectar a la máquina host a través del puerto de depuración, como se describe en Cómo escribir en la memoria flash del nRF52840. Para ejecutar el sniffer de Pyspinel, usa la marca -b para especificar la tasa de baudios (si se cambió de la predeterminada) y omite la marca --no-reset.
Si configuras Wireshark para mostrar RSSI, también debes incluir la marca --rssi cuando ejecutes la herramienta de sniffer. Por ejemplo, para husmear en el canal 15 con un dispositivo montado en /dev/ttyACM0 con RSSI incluido en el resultado de Wireshark, haz lo siguiente:
cd path-to-pyspinelpython sniffer.py -c 15 -u /dev/ttyACM0 --crc --rssi -b 460800 | wireshark -k -i -
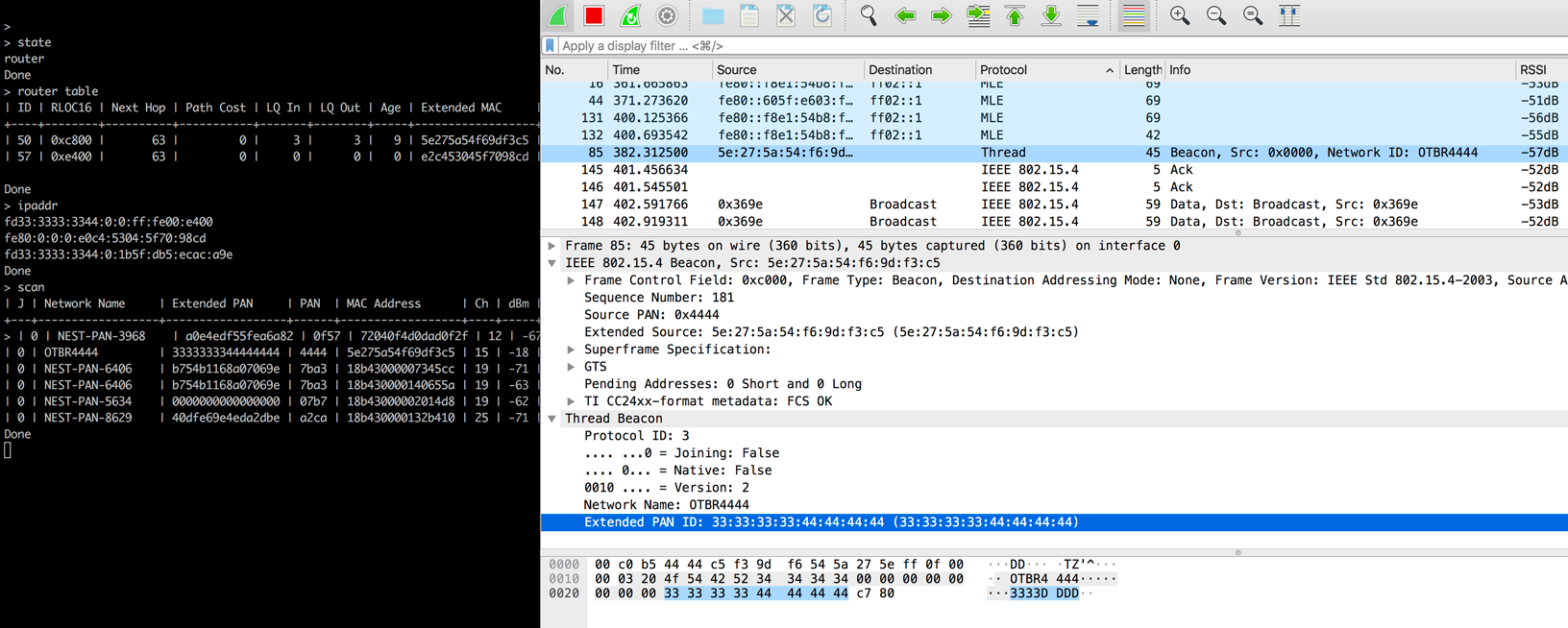
Ahora deberías poder ver los paquetes y los protocolos relacionados con esta configuración en Wireshark:
Consulta la referencia del sniffer de Spinel para obtener más información sobre cómo ejecutar el sniffer de Pyspinel.
Conexión USB nativa
Para usar el puerto USB del nRF52840 DK, se requiere que el objeto binario ot-rcp de OpenThread se compile con USB_trans:
./script/build nrf52840 USB_trans
--no-reset, pero omite la marca -b cuando ejecutes el sniffer:
python sniffer.py -c 15 -u /dev/ttyACM0 --crc --no-reset --rssi | wireshark -k -i -
Recursos
Para obtener herramientas adicionales de Nordic, consulta Nordic Semiconductor: sniffer de Thread basado en nRF52840 con Wireshark.